Catch security gaps before you ship
We analyze your product, map out risks, and give a
clear checklist of fixes so you can launch with confidence.
Amazon secures their codebase based on these practices
Why founders & security teams choose us
Move fast, stay safe
Model threats alongside your roadmap so security never becomes a blocker.
Actionable over academic
Clear risks, impact, and fixes mapped directly to issues—not 80-page reports.
Built for collaboration
Product, eng, and security work from the same source of truth.
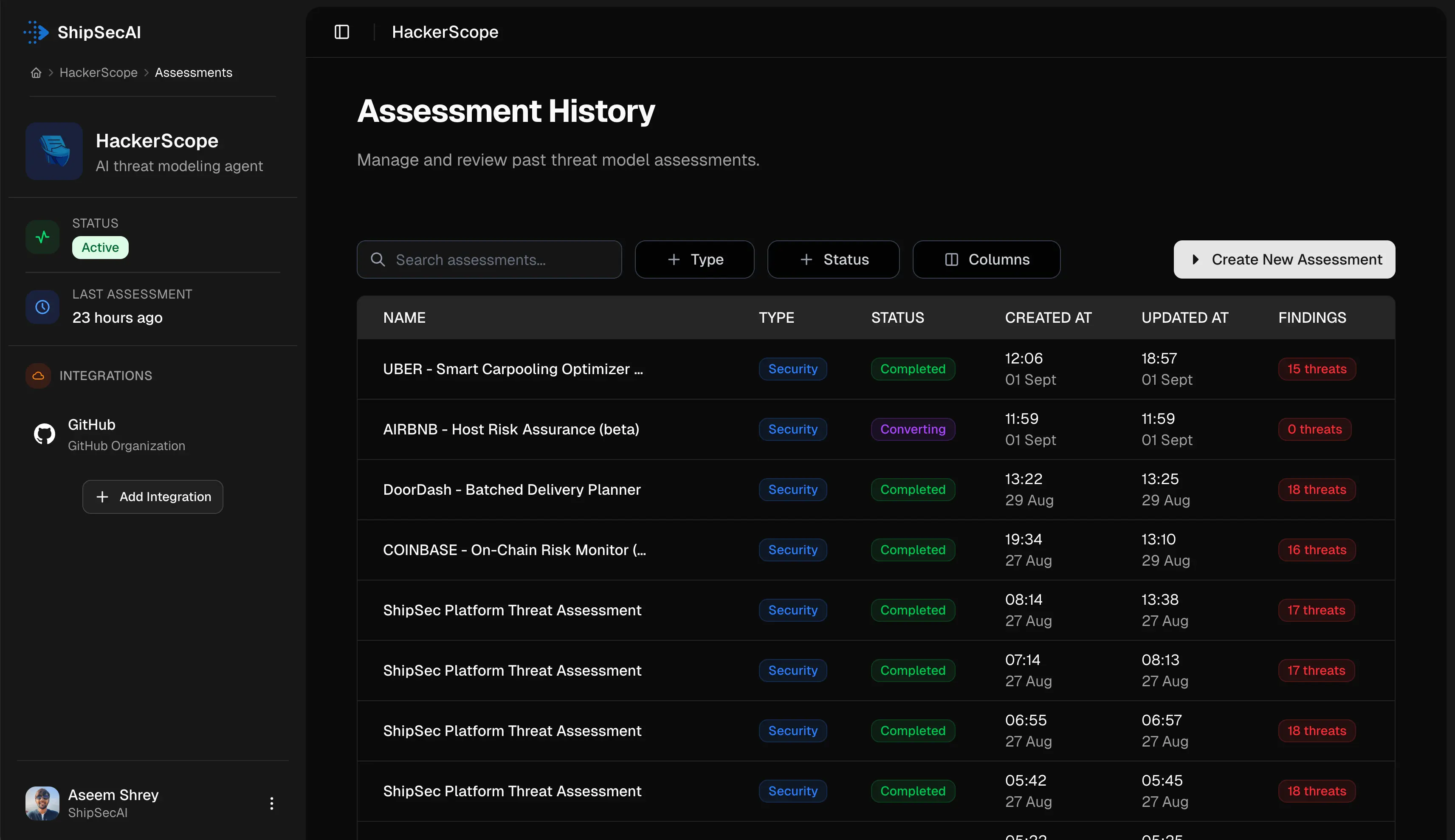
How it works
Three simple steps to get your comprehensive threat model and security checklist
Step 1: Bring your context
Step 1: Bring your context
Drop in anything: Notion doc, PDF, README, summary/text file, architecture diagram, or screenshot. We extract flows, entities, and assumptions automatically.
Supported formats:
Step 2: Threat modelling based on STRIDE / LINDDUN
Step 2: Threat modelling based on STRIDE / LINDDUN
Industry standard privacy and security risk assessment using proven frameworks trusted by security professionals worldwide.
Industry standards:
STRIDE
Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege
LINDDUN
Linkability, Identifiability, Non-repudiation, Detectability, Disclosure of information, Unawareness, Non-compliance
Step 3: Checklist of Actionable items
Step 3: Checklist of Actionable items
Get a prioritized list of actionable security findings with clear remediation steps. No more 80-page reports - just what you need to fix.
Example findings:
Built for Modern Teams
Model, map, and fix: STRIDE/LINDDUN, attacker diagrams, real scenarios, simple checklist.
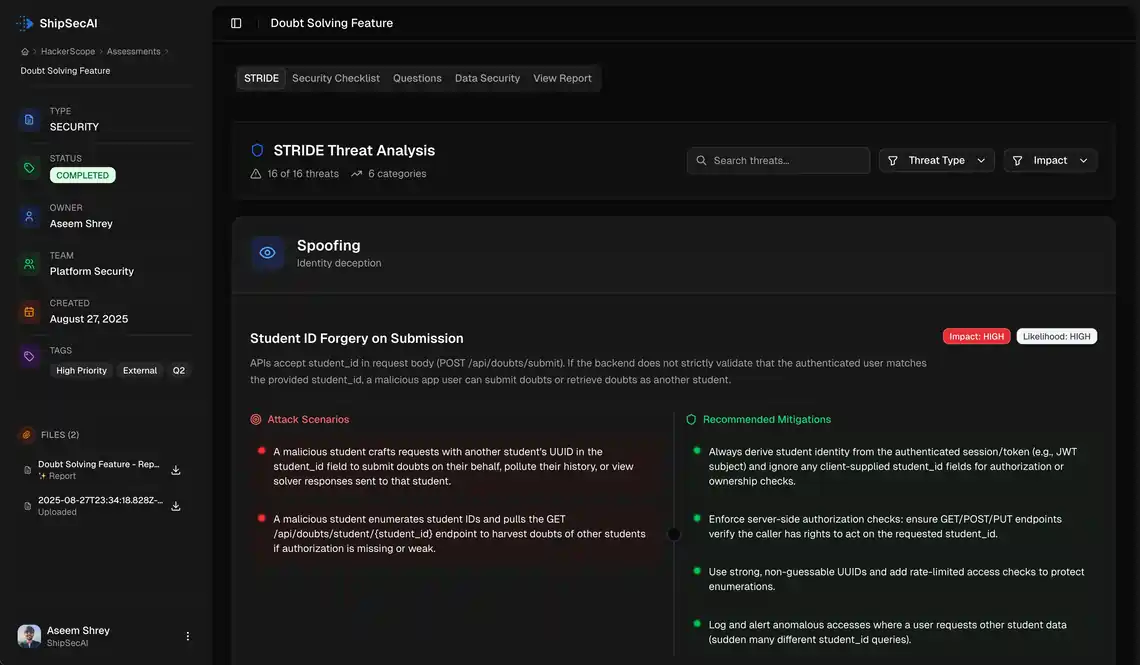
STRIDE Security Analysis
Comprehensive threat modeling using industry-standard STRIDE framework to identify spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege risks.
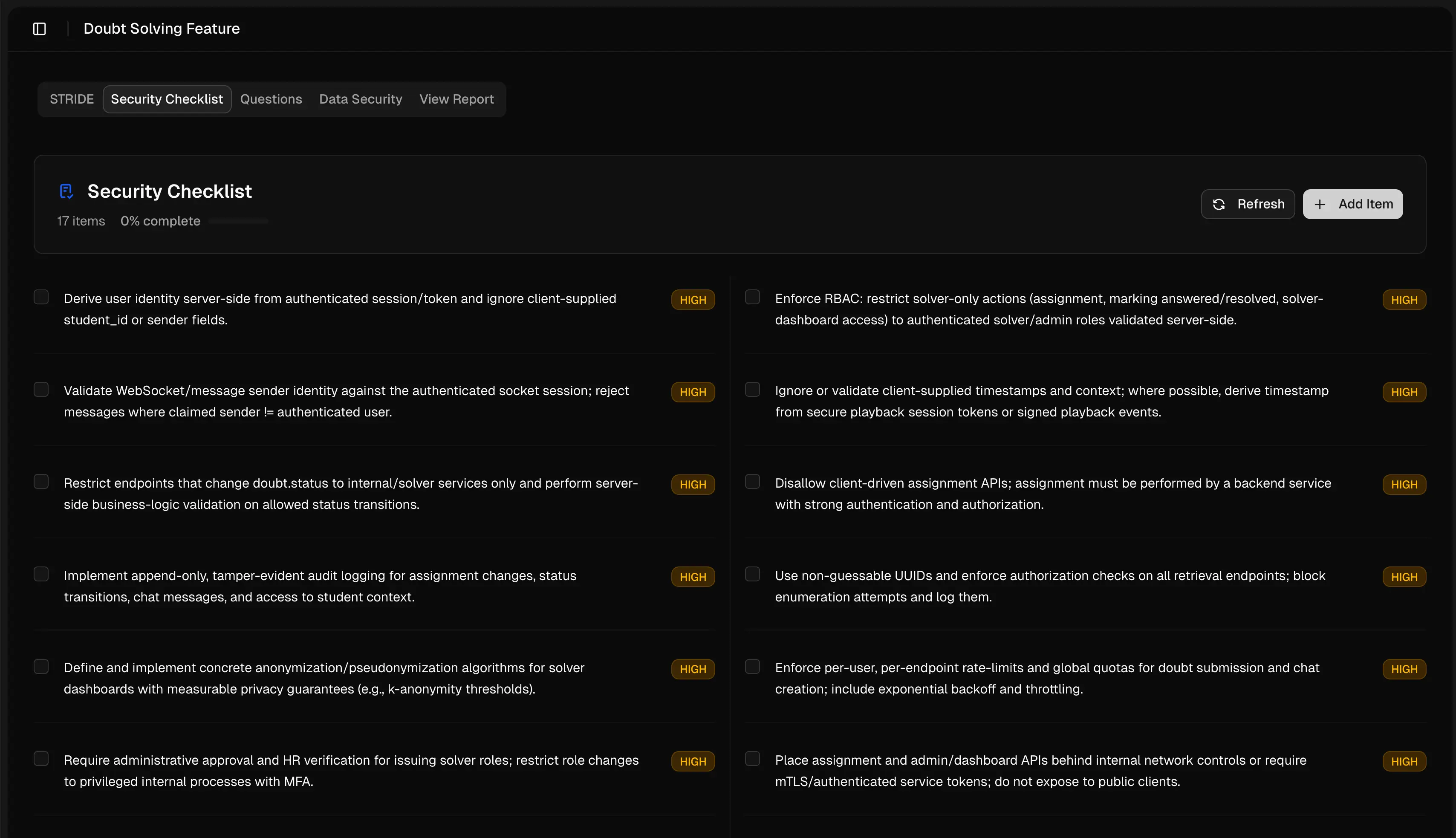
Security Checklist
Actionable security items prioritized by risk and impact, with clear remediation steps.
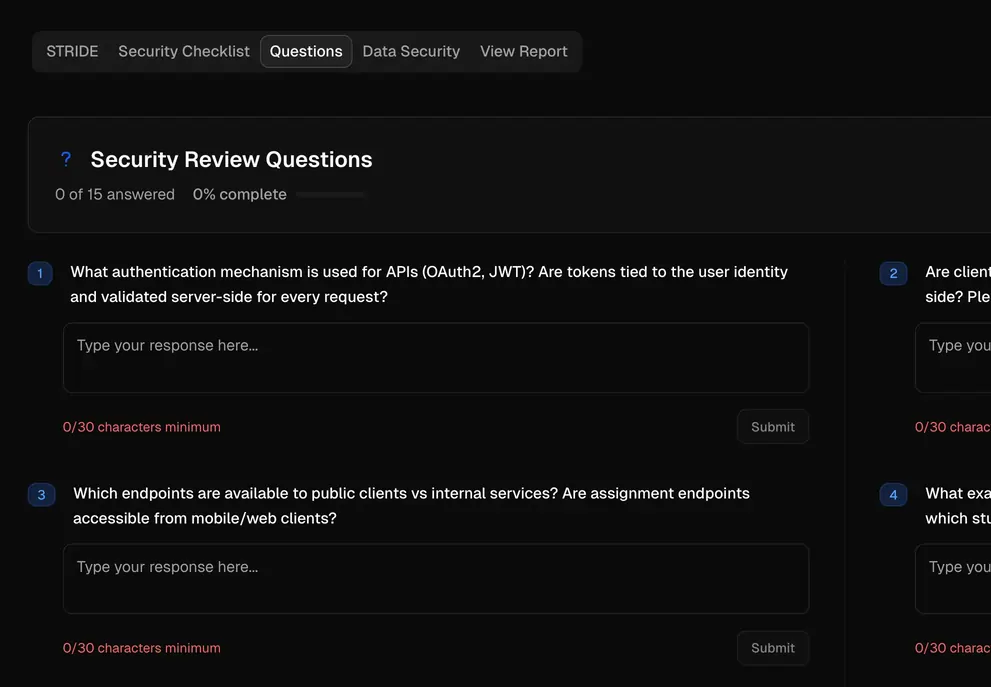
Questions & Analysis
Smart questionnaire that guides you through security considerations specific to your architecture.
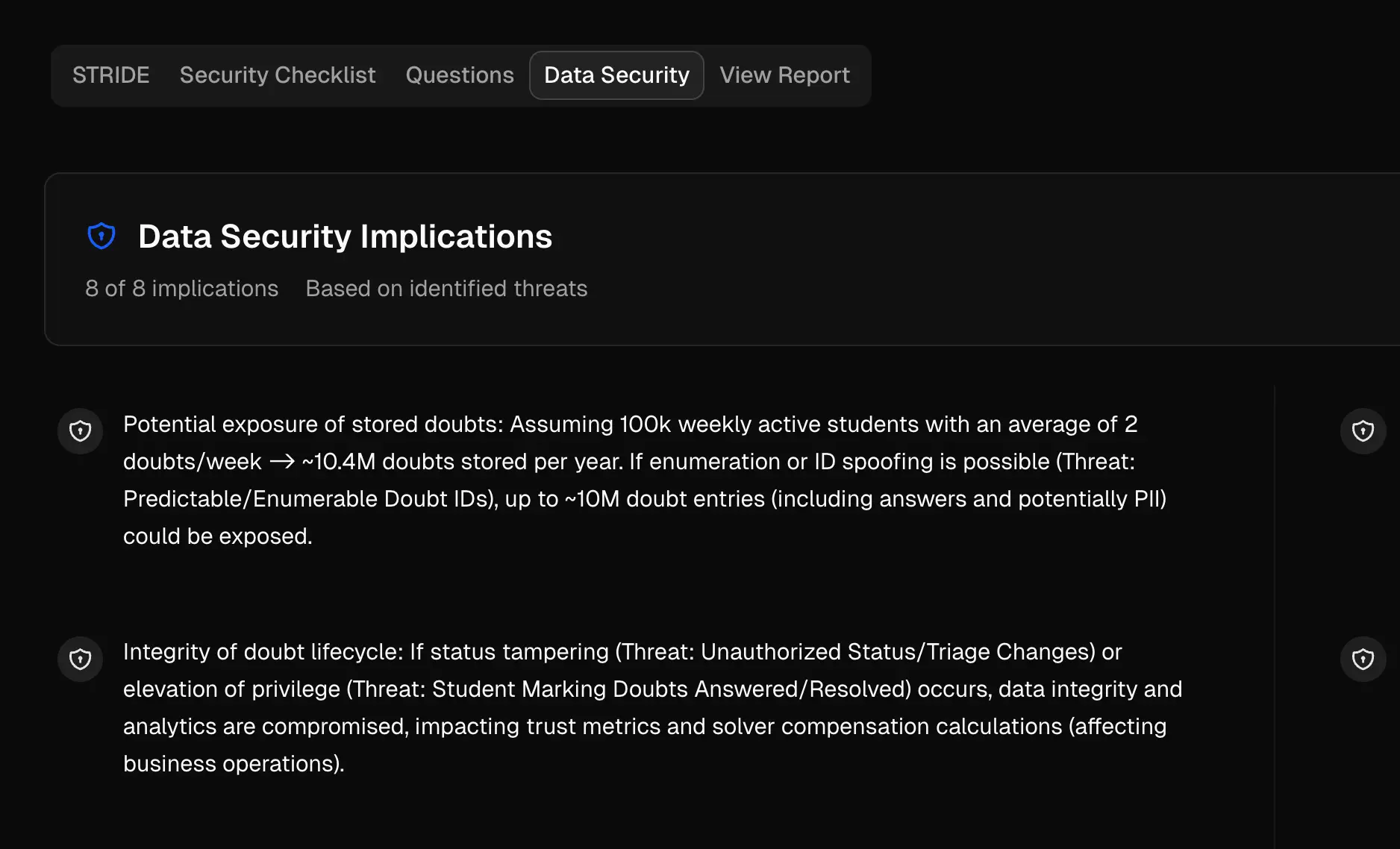
Data Security Overview
Map data flows and identify privacy risks with LINDDUN methodology for comprehensive data protection.
Real World Attack Scenarios
Insights from hacking experience of over 10 years.
Real Attack Vectors
10+ years of hacking experience
Frequently Asked Questions
Everything you need to know about threat modeling
Who is this for?
We already scan for vulnerabilities. Why this?
What does early access include?
Why do I need to do this?
The Founders
Meet the experts behind ShipSec
Ship with fewersecurity surprises
Get your security review in minutes.

